Vulnerability Management Essentials
Vulnerability Assessment Overview
The evolution and a large volume of cyber-attacks scare many security teams. Understanding the security risks and current threats helps to address them. Most cyber-attacks take advantage of unknown and hidden flaws. These cyber-attacks make vulnerability assessment software the most crucial step to protect organizations.
Before we dive in, let us understand “what is vulnerability assessment.”
What is vulnerability assessment?
Vulnerability Assessment is a process of identifying, assessing, and prioritizing vulnerabilities. It involves analyzing IT to find potential risks present in organizational assets and aids in the remediation of vulnerabilities.
Now we are aware of “what is vulnerability assessment.” Most enterprises are in a dilemma about how vulnerability assessment is different from management.
Some common questions asked by enterprises are,
- Are vulnerability management and assessment related?
- If related, how?
Difference between vulnerability assessment and vulnerability management
Vulnerability Assessment
Security vulnerability assessment is an automated process of identifying and prioritizing vulnerabilities. There are different kinds of vulnerability assessments, and, depending on the assessment tools used, this process can take days, weeks, or even months.
It is similar to vulnerability management but with a slight difference. Without repeated vulnerability assessments, there is no real vulnerability management.
Vulnerability Management
Vulnerability management is a continuous process of vulnerability assessments but with remediation. It takes place at regular time intervals. In vulnerability management, you can measure progress, determine security risks, and remediate them.
Now you know the difference between them. Let us focus on the importance of vulnerability assessment.
Importance of assessing vulnerabilities
Vulnerability assessment makes the process of vulnerability management easier. It is important to analyze your IT landscape continuously in order to protect it from cyberattacks. This initial step is crucial for understanding the extent of vulnerabilities and their impact on the organization, enabling organizations to allocate resources efficiently toward remediating the most critical threats
Furthermore, it helps in allocating resources accurately for focused remediation and also helps in cost savings. Additionally, Vulnerability assessments are mandated in most regulatory bodies and organizations to ensure adherence to cyber laws.
The process of effectively Assessing Vulnerabilities
Asset inventory
Asset inventory is the foundation of complete IT security. Without clear visibility over IT assets, protecting them will be difficult. Understanding the environment and its assets will aid in better security vulnerability assessment.
Rapid scans
Scanning is the primary process of identifying vulnerabilities. Most organizations rely on periodic scanning, which takes place once or twice a month, making IT more prone to cyberattacks. Hence, scanning should be a daily ongoing process to manage vulnerabilities and should be done within minutes.
Accurate detection
Vulnerability detection marks the foundation for assessing vulnerabilities. If the detection is not accurate, the assessment data will not be precise. For accurate detection, there is a need for an effective vulnerability scanner that detects vulnerabilities and other security risks without producing false positives. An inefficient vulnerability scanner drains the security team’s energy in assessing false positives.
Predictive risk analysis
Predicting vulnerability exploits before they show up is one way to manage vulnerabilities. You can improve security posture by predicting the probability of new exploits andanalyze the recorded occurrence and probability of recurrence. Thus, it can estimate the nature of emerging vulnerabilities.
- Intact prioritization
After detecting the vulnerabilities, we need to rank them based on severity levels. CVSS, business context, technical impact, and risk-based assessment will help in precise prioritization. Prioritization aids in remediating the high critical risks first. The combination of CVSS and risk-based assessment is even more effective.
- Instant remediation
Detecting the vulnerabilities is on one side, and remediating is on the other. After detection of vulnerabilities, remediation of vulnerabilities will reduce potential attacks. Most organizations lag in remediating vulnerabilities on time and going for an integrated vulnerability and patch management solution with help here.
Introduction to Vulnerability Assessment Tools
Vulnerability assessment tools find security threats across systems in enterprises. In addition, vulnerability assessment tools prevent unauthorized access to the systems from attackers. These tools scan the entire organization network for weaknesses and quickly start the remediation process. Hence, security vulnerability assessment tools aid in effective vulnerability management.
How to find the best tool to assess vulnerabilities?
Vulnerability Assessment with SanerNow
Vulnerability assessment should always be the quickest stage of your program. To make sure, you need the best vulnerability assessment software. Assessing vulnerabilities with manual research makes security teams commit errors during the assessment.
Your attack surface will suffer the consequences due to errors. The ideal cyber vulnerability assessment tool is an all-rounder in all crucial functions.
Let us find out how SanerNow makes all the above a simple process.
- Rapid scanning techniques
Vulnerability scans determine the efficacy of assessing vulnerabilities. The faster and accurate it is, the better the assessment results. Make sure that you opt for a tool that runs the fastest vulnerability scans.
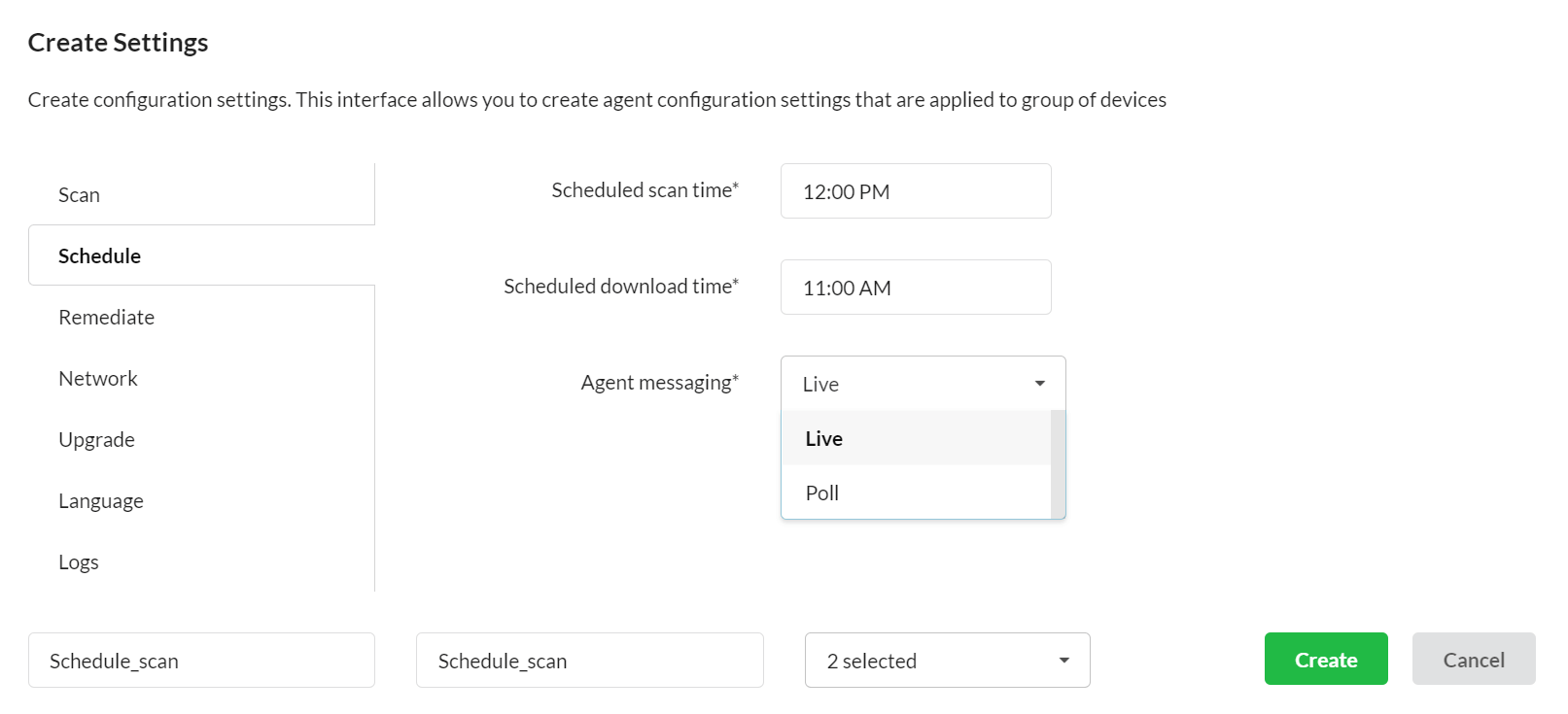
SanerNow provides the industry’s fastest vulnerability scans, in less than five minutes. Its intelligence-augmented, efficient scanning algorithm makes scanning rapid. In this time frame, you can scan any number of devices with SanerNow. In addition, you can also choose to schedule and automate these scans.

Fig 1: Configuration Settings - Large and Extensive database
The success of a scanner lies in the accuracy of detection. A vulnerability scanner that gives false positives will let down your security program. For accurate detection, you must integrate your scanner with a large vulnerability database. The database must hold the most number of security checks, and it should be up-to-date.
SanerNow leverages its home-grown world’s largest vulnerability database of around 190,000+ vulnerability checks. SanerNow’s vulnerability intelligence feed is regularly updated with the latest vulnerability details.
- Wide asset coverage
Broader security vulnerability assessment requires a wide coverage of vulnerabilities in the database. Some tools support only one or a few platforms, like Windows or Linux, and some tools do not support all devices in the network. In addition, without coverage to every nook and corner of your network, you can not prevent exploits. Make sure that you go for a scanner that supports all devices.
SanerNow vulnerability management supports all IP-enabled devices in the network. It also supports all operating systems like Windows, macOS, and Linux. Thus, no device or operating system can escape SanerNow’s eyes.
- Automatic and predictive prioritization
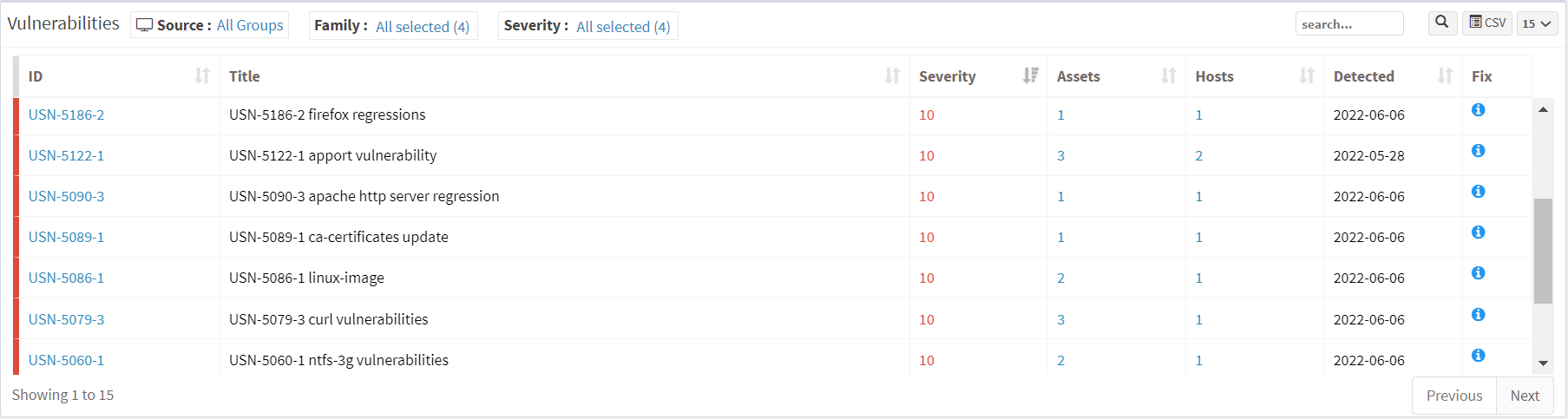
Prioritization is an important step while assessing vulnerabilities. It helps you prioritize vulnerabilities based on their severity level. This method tells you what to remediate first, saving you from spending your efforts on less critical vulnerabilities.
Fig 3: Vulnerabilities
SanerNow instantly prioritizes the vulnerabilities based on their severity range. It depends on CVSS scores and risk-based vulnerability management techniques that will help to rank vulnerabilities. With intact prioritization results from SanerNow, you can smartly plan your remediation.
- Integrated patch module
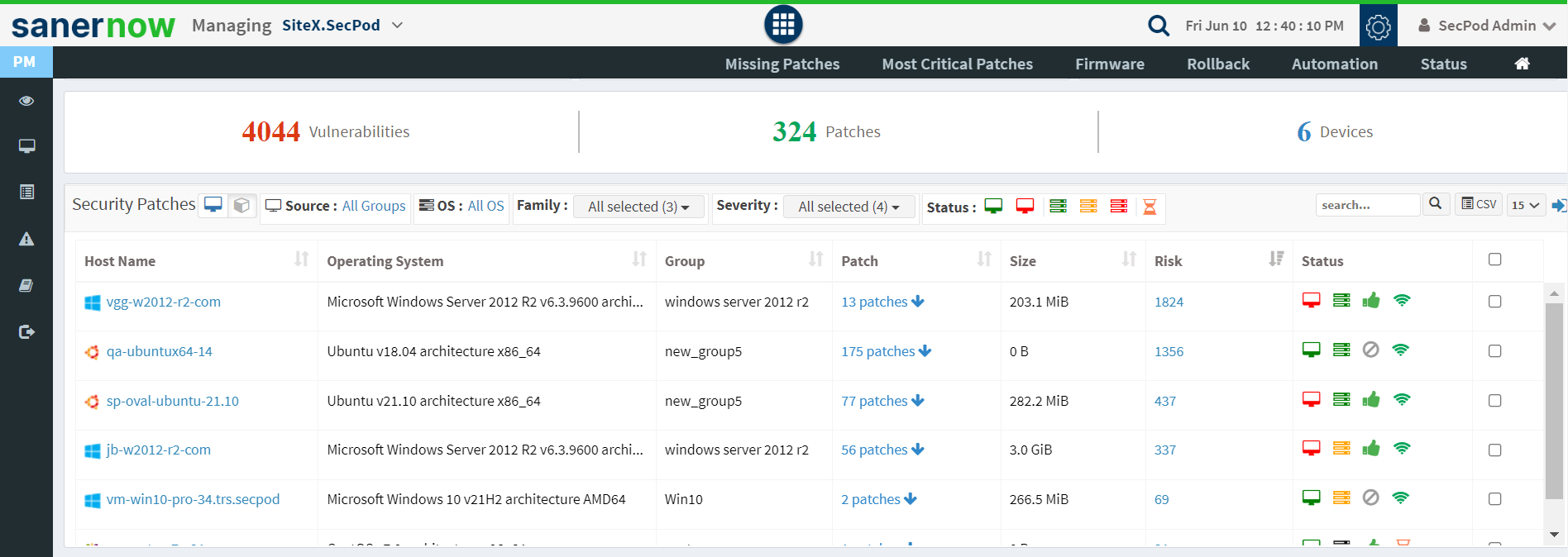
Without remediation, you have not won the battle of security vulnerability assessment. The remediation has to be fast enough to prevent security gaps. Opt for an integrated patch management solution to remediate vulnerabilities quickly.
Fig 4: Vulnerability Assessment Dashboard
SanerNow provides an integrated vulnerability and patch management solution. You can execute all steps from scanning to remediation from one place. SanerNow supports patch remediation for all OSs like Windows, macOS, and Linux. In addition to this, it also supports patches for 550+ third-party applications.
- Customizable reports
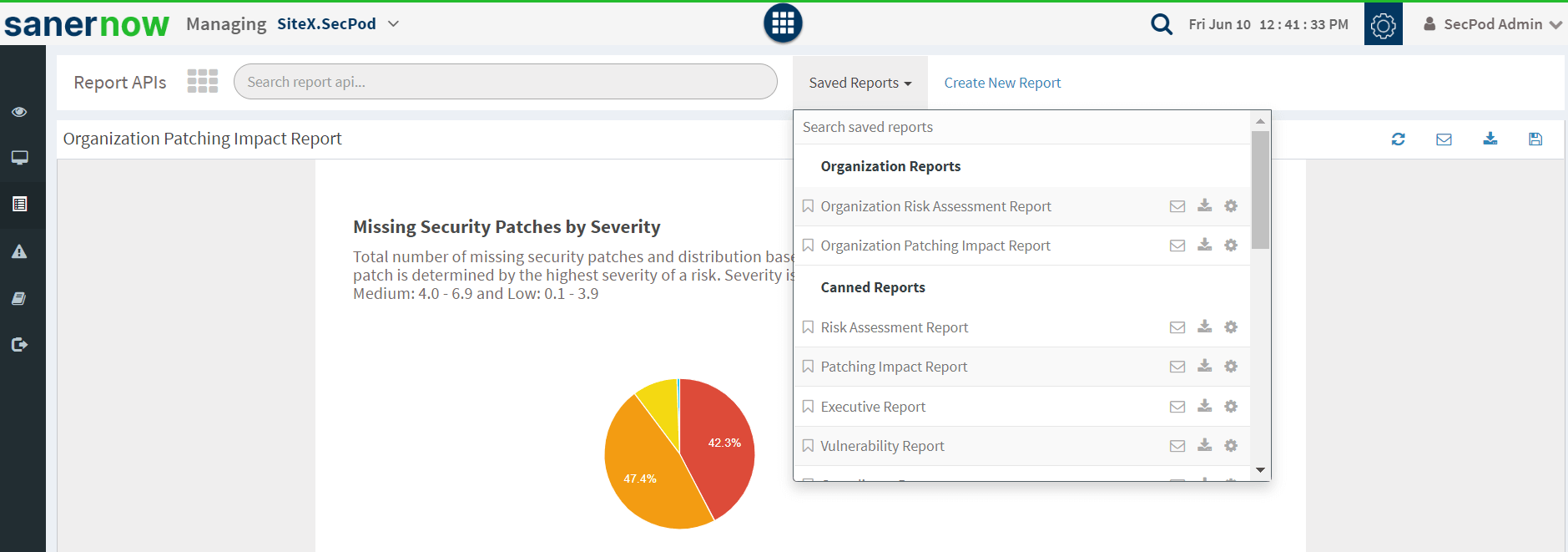
Reports help in smart security vulnerability assessment and evaluation. Insightful reports are important to assess the whole process and the vulnerability details. Hard-to-read big reports are not easy to understand. Pick a tool that provides good reports.

Fig 5: Customizable Reports
SanerNow provides customizable and insightful reports. You can quickly assess the vulnerability management process with these reports. Also, pre-built reports are available in SanerNow for assessment These reports can be automated and scheduled. Besides, you can configure and receive these reports in your mailbox. In your search for the best vulnerability assessment tools, SanerNow will be the best fit to assess and manage your network vulnerabilities. If you have not seen SanerNow in action yet, schedule a demo now.