A New Dimension to Cybersecurity:
Continuous Vulnerability and Exposure Management (CVEM)
Transforming the Approach to Cyberattack Prevention
Allow us to introduce a novel approach to cybersecurity – one that promises to fortify our defenses, creating a robust posture capable of fending off cyberattacks.
To understand this perspective, we want to emphasize a fundamental truth that applies to every form of attack, whether in the physical world or the digital realm: every attack involves the exploitation of a weakness. Whether executed by a thief, a burglar, a goonda, a rowdy, a terrorist, or a state-sponsored actor, the common thread is the exploitation of a weakness. This holds true both in the physical world and the cyber domain. From black-hat hackers, script kiddie, hacktivist, malicious insider, to state-sponsored entities, they all operate by exploiting weaknesses.
Whether it is Malware, DDoS attacks, phishing, spoofing, and a plethora of other tactics are all refined to exploit specific weaknesses, technological, people, or process weakness.
Every Attacker Leverages a Weakness
Let’s engrave this truth in our minds and on our walls: Every Attacker Leverages a Weakness, be it in our cyber defenses or physical security measures. There is no room for negotiation on this front.
Understanding this perspective shifts how we approach cybersecurity. It introduces a new dimension. We begin actively seeking out these weaknesses, gaining a deeper understanding of our infrastructure – a crucial aspect of cybersecurity. This new perspective can be the key differentiator between us and the attacker.

Weakness Perspective and Analysis
The weakness perspective involves the
assessment of IT infrastructure that encompasses Devices, Applications,
Users/Identities, Data, Networks, and Security Controls.
With this perspective, you’ll,
- Study your IT infrastructure, get granular visibility to everything
- Know your weaknesses and devise controls
- Know how your controls are functioning
- Know where your sensitivity exists
- Ask a lot of ‘why’ questions
- Evaluate all your security controls
- Identify gaps and learn about your strengths
- Feel empowered
Detection Perspective: It often relegates itself to a secondary role, presuming attacks are imminent and formulating strategies for countering them either during or after the attack. However, countering proves to be a monumental challenge, given the staggering diversity in attack methodologies, resulting in a near-certainty of oversight. I am making an important point here, ‘detection is secondary’, while the entire industry is focusing on detection.
Data Perspective: It places data at the core of every consideration, advocating for the implementation of measures to safeguard this invaluable asset. Yet, it grapples with parallel challenges to the Detection Perspective. Moreover, there’s a crucial recognition that while data holds great importance, it does not encompass the entirety of an attack scenario.
Attacker Perspective: It encounters its own constraints, stemming from the intricate nature of modeling every potential attacker and predicting their behavior, especially when there is a lack of a standardized method for characterizing attackers.
Device, Application, Network, and User Perspectives: Each provides a valuable but limited viewpoint in the complex landscape of a multi-dimensional cyberinfrastructure.
Weakness Perspective: Embodies everything, barring the Detection Perspective. To study your weaknesses, you’ll study your devices, your network, your data, your software, your users and their privileges, your security controls, your network, your attack surface, your threats, and potential attackers.
It is imperative that we turn our attention towards these weaknesses and prioritize them in our cybersecurity measures. We term these weaknesses ‘vulnerabilities’, a concept familiar to us through Vulnerability Management. However, despite our efforts, attacks persist. Why is this the case?
Before delving into this question, let’s first distinguish between two critical terms: “vulnerability” and “exposure”.
Vulnerability Vs Exposure
In the industry, I’ve noticed these words are often used interchangeably. Furthermore, there’s a growing perspective that exposure management represents an elevated version of vulnerability management.
Consider this: when a vulnerability is exposed, it transforms into a potential threat. Therefore, risk can be quantified as the probability of a threat exploiting a vulnerability, multiplied by its exposure.
Threat = Vulnerability x Exposure. So, Risk = Probability of Threat (Vulnerability x Exposure))
To gain a comprehensive understanding of threat dynamics, it is paramount to analyze vulnerabilities and exposures both independently and in combination. This nuanced examination provides invaluable insights into the potential risks an organization may face.
Coming back to our question, Why Vulnerability Management isn’t effective?
Why Vulnerability Management isn't Effective?
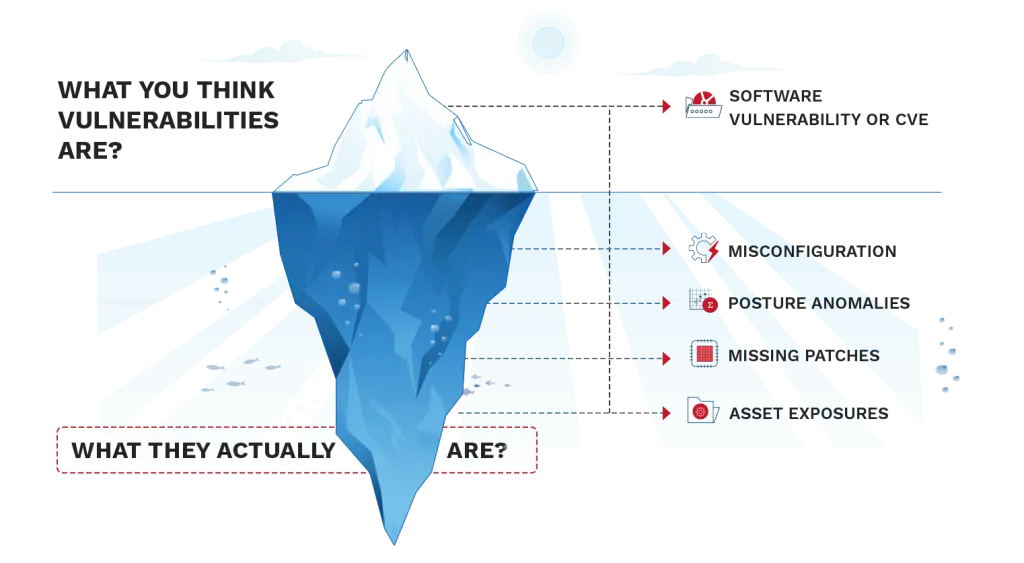
- Firstly, our focus often narrows down to what we commonly refer to as ‘software vulnerabilities’. While undeniably crucial, they represent only a portion of the vulnerabilities attackers are keenly aware of. Even here, our efforts fall short. Timely discovery and mitigation are often lacking, and we tend to rely on point solutions. It is not continuous, nor automated.

- Secondly, a whole array of vulnerabilities often
escapes our scrutiny. Misconfigurations, non-functioning security controls,
unwanted or unnecessary IT components, posture anomalies – the list goes on.
These hidden vulnerabilities are what attackers exploit, often with devastating
consequences.
Why is Your ‘Traditional’ Vulnerability Management Software Not Effective?

Lack of Deeper Insights into the IT Infrastructure
IT security teams don’t have enough visibility of their IT infra. The traditional tools don’t give teams the details of potential risks and the teams might miss out on big risks. You can’t secure your IT if you can’t see all your assets.

Vulnerabilities Beyond CVEs are Left Out
Most traditional tools only deal with known software vulnerabilities (CVEs), ignoring other security risks. These risks are IT asset exposures, misconfigurations, missed patches and security controls deviations, and security posture anomalies.

Lack of Integrated Remediation Capabilities
Without remediation capabilities, traditional tools are only going to make vulns stay in your system, giving attackers the opportunity to exploit them.

Siloed Interfaces and Multiple-Point Solutions
Old-fashioned solutions use separate tools to handle different goals of vulnerability management process. Switching between these tools is tough, slow, and demands a lot of manual work.
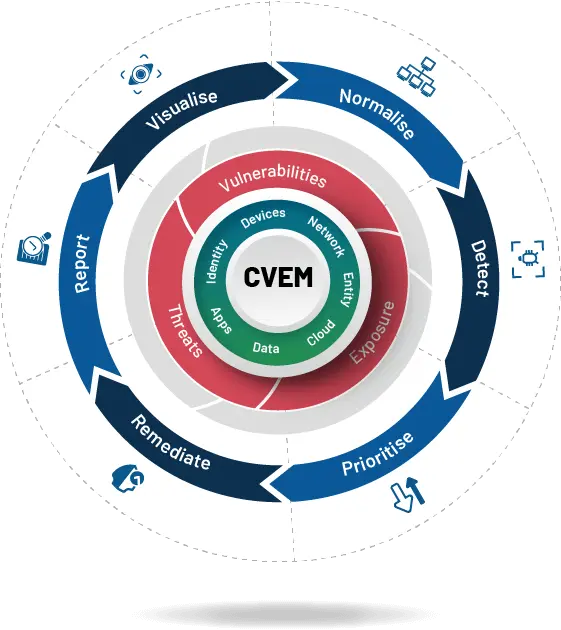
What is Continuous Vulnerability Exposure Management (CVEM)?
Continuous Vulnerability and Exposure Management (CVEM) introduces a fresh perspective to cybersecurity by evaluating an organization’s IT infrastructure security status from a Weakness Perspective and allowing it to strengthen its security posture capable of defending against cyberattacks.

An end-to-end vulnerability and exposure management comprising Visibility, Normalization, Detection, Prioritization, Remediation, and Reporting must be implemented at each infrastructure layer.
Spot the Difference with Continuous Vulnerability and Exposure Management
Traditional Vulnerability Management
Continuous Vulnerability and Exposure Management
Visibility to limited IT asset details with insufficient actionable insights
Holistic and deeper visibility into IT infrastructure with clarity on actionable insights
Siloed interfaces & multiple-point solutions approach
Unified, single-solution approach to visibility, detection, assessment, prioritization, and remediation
Rely on a separate tool for remediation
Integrated and seamless patch management capability for timely remediation
Discover only CVEs or software vulnerabilities
Detect vulnerability, misconfigurations, asset exposures, missing critical security patches, and security posture anomalies within a single console
Lack of remediation controls to fix security risk exposures
Remediation controls beyond patching to fix the vulnerability and other security exposures
Manual methods and irregular processes
Built for automation, achieving continuous compliance
Irregular scans and no clarity on real-time risk posture
Continuous scan and up-to-date risk posture assessment
Prolonged Patch Management Lifecycle taking months to complete
Rapid, continuous, and automated patch management lifecycle
Lack of capabilities to build queries to detect and respond to security risks
Build custom queries to detect security risks and deploy instant response
Limited OS and device-specific support
Heterogeneous and device-agnostic support
Multiple agents that delays processes
Single, light-weight, multifunctional agent
Lack of API support & eco-system integration
Native API support and eco-system integration
Ineffective attack surface management
Rapid and effective attack surface management
Lack of weakness perspective for cyberattack prevention
Weakness perspective incorporated into managing security risks.
Segregated security & IT goals
Unified security and IT goals
Conclusion
Consider the implications when an attack surface is vast, and an oversight in a seemingly obvious area leads to a catastrophic breach. This is why it’s imperative that we shift our focus. Vulnerability management, attack surface management, and exposure management must take center stage in our cyber defense program. It is through a comprehensive understanding of these vulnerabilities and a proactive approach toward shoring up our defenses that we can truly safeguard our digital realms.
Every attacker exploits a vulnerability. Bring true Vulnerability and Exposure Management to the forefront and make it continuous and automated. Rethink cybersecurity from the weakness angle.
Key Resources
A New Dimension to Cybersecurity:
Continuous Vulnerability and Exposure Management (CVEM)
Watch this webinar where we discuss:
- Are vulnerabilities and exposures same?
- Is detecting ‘software vulnerability’ enough?
- What is ‘Management’, when it doesn’t include remediation?
- Shouldn’t vulnerability, exposure, or weakness management be ‘Continuous’ as well?






